Exploit Reveals a Blind Spot in the Global Digital Supply Chain

Similar to the lingering symptoms experienced post COVID, Log4j poses a risk for the foreseeable future. Security professionals agree that even systems that have recovered from the exploit, may still face certain risks regardless of the exploit no longer being present.
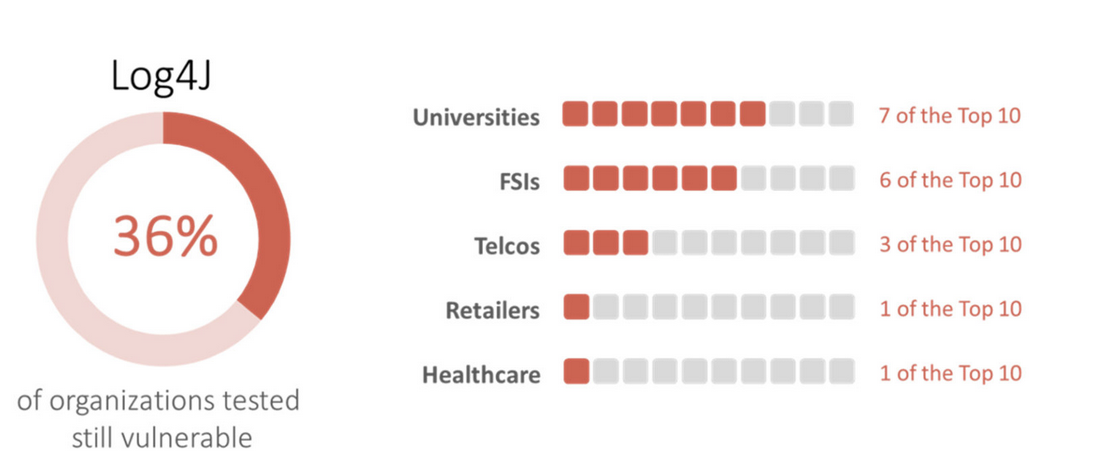
“In February we found that 36% of the 50 organizations analyzed remain vulnerable to the Log4j vulnerability with specific verticals like retail and healthcare fare well, while universities and financial services fare poorly.”
CQ Prime Threat Research Team
Based on statistics, even once a globally known vulnerability is disclosed and patched organizations sill suffer from a lack of implementation. This points out one of the largest draw backs to threat response. Even if a potential threat is discovered and a means of protection is created, it all means nothing if the solution is never utilized.
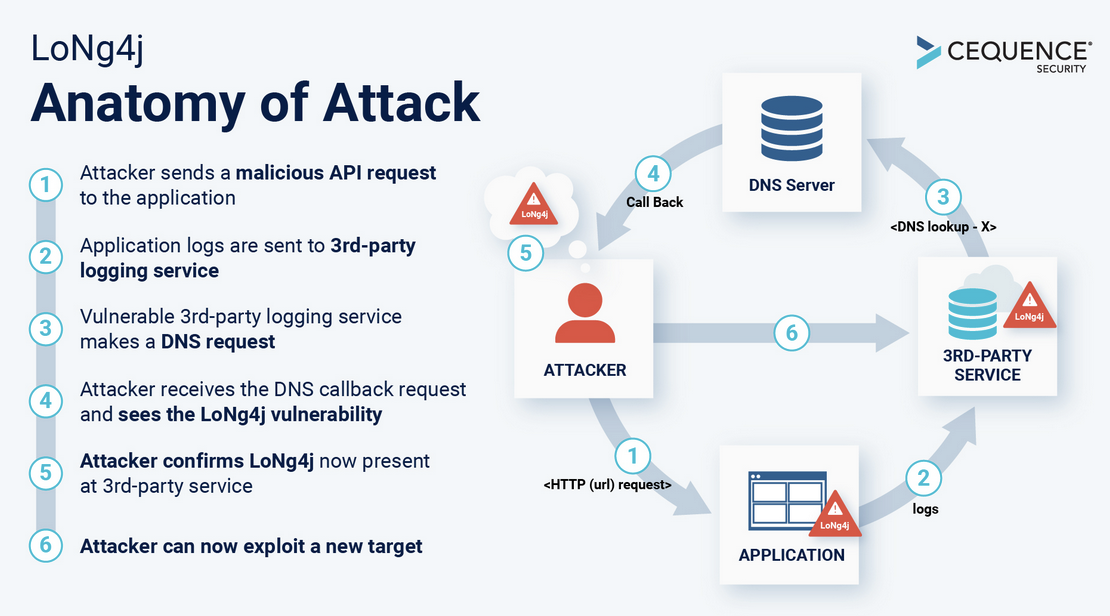
How does Log4j Exploit Testing work?
The main way to figure out if an application has the Log4j vulnerability is present is by embedding a malicious domain look up request. From there the vulnerability logging component will generate a DNS query. The DNS query is what confirms that the logging component is vulnerable and from there security professionals are able to conclude there is a high likelihood that the vulnerability exists. From there specialized scanning is required to determine further details about the vulnerabilities existence.
With over 20+ years in the trucking insurance industry Cook Insurance Group combines national reach with local service to address the needs of large fleet, small fleet, single owner and tow trucking operations, and to charter bus lines. We ONLY serve the Trucking industry, providing the best trucking insurance. Let our friendly, bi-lingual staff help you find the right insurance protection at the right cost.
Cook Insurance Group is dedicated to meeting the needs of both small and large fleet trucking companies. Our reps handle every aspect of your program, ensuring you have the best trucking insurance plan for your specific needs. We work closely with you to manage your plan on an ongoing basis.
At Cook Insurance Group, we provide immediate certificate and ID card insurance, including 24/7 certificate availability. We leverage our client portal which allows you to access and issue certificates, check claim status and view policies. Cook Insurance Group is prompt and reliable, including 24-hr claims reporting. (Physical Damage and Motor Truck Cargo). We also provide educational seminars for management and drivers of companies.
At Cook Insurance Group we have licensed risk managers available to assist you with CSA scores and driver training. We provide border risk coverage (NAFTA) and mid-year loss run reviews.
Choose Cook Insurance Group for all of your trucking insurance needs whether you are located in Texas, Arizona or Arkansas.



